Our vacancies per sector
We are pure players in cybersecurity. Our team of experts therefore delivers a top-quality engineering service, in line with the business constraints of our corporate customers.
Since our inception, we decided to devote our cyber expertise to a few areas of business including critical and embedded systems.
We are therefore very much aware of all of your business constraints and apply them to every step of the support process, whatever your needs.
We have created Skills Centres in order to ensure responsiveness and relevance when choosing our engineers, for the missions you entrust to us.

Our skill centres
Benefiting from our Skills Centre means having the best profiles in our various divisions, according to the context of your business. We have a multi-skilled team (hacker, functional, risk analysis, architecture, developers, CDP, etc.) dedicated to your project. The benefits: we mobilise the right skills at the right time for you; our top professionals are made available to you, your project is well-structured and we work very closely with your team.
AERONAUTICS AND AIR TRAFFIC CONTROL
Security by Design and assessment of critical air navigation infrastructures and systems & securing aircraft components within the framework of its certification.
AUTOMOTIVE
Risk analysis, securing and assessment of embedded automotive, public transport and cloud components on the specific vehicle.
FORENSIC
Our Computer Forensic Laboratory houses all the tools and skills necessary to manage security incidents and to file complaints.
IOT INDUSTRIAL
Today's R&D department produces tomorrow's tools to improve the security of IoT systems at the level of equipment, connections and cloud backend.
HEALTH AND PUBLIC SECTOR
We support health care facilities in their GDPR compliance and achieving ISO 27001 HDS certification, in line with the priority of data protection and patient care protection.
DEFENCE AND SPACE
Our Centre of Expertise and Excellence makes multidisciplinary engineers available to players in the space sector, capable of meeting the specific needs of the sector in terms of the accreditation of systems, ground segments and cybersecurity (GNSS and EGN).
Our engineering expertise
Management of skills
In order to constantly maintain a high level of expertise and qualification as well as a competitive advantage, SCASSI is committed to permanently improving the skills of its employees.
We are particularly mindful of monitoring our employees via our HR processes. The skills are monitored by the Managers of our 3 divisions (Architecture, Governance & Conformity, Technical Evaluation). This monitoring results in technical and functional qualifications/training courses, which often leads to certification being achieved over a period of one year.
Internal promotion forms an integral part of the SCASSI company culture and most of our technical managers originated from our talent pool.
Management of the risks and conformity of the information systems is essential when working in numerous industries. It must be systematically implemented and organised to ensure full control of the operations. SCASSI engineers advise you through every step of the process, from diagnostics right through to implementing, inspecting and improving your equipment, in order to ensure they conform with the regulations and your risk management policies.
SCASSI supports you in implementing a security management system through an approach based on the risk analysis.
Our cybersecurity technical skills
- EBIOS risk analysis on a complete system
- Risk analysis, definition and processing of security requirements on dual systems (civil/military)
- Risk analysis on business referentials (e.g. TARA)
- Compliance with the French Committee for Banking Organisation and Standardisation (CFONB) for online banking systems
- ISO 27001 HDS certification support
- Organisational and physical audits
- Support with designing secure software architecture
- Performance of “custom” risk analyses or packaged offers
- Securing the processing of personal data (CNIL, GDPR)
- Analysis and support for regulatory and normative compliance: ISO 27001, MPL, ii901, GDPR, RGS, HDS, PCI-DSS
- Security process: approval of IS, security in projects, access management, etc.
- CISO coaching and security policies
- Security guidance and management (indicators, dashboards, master plans, etc.)
- BCP and BRP: emergency strategies, steering, crisis management
- Provision of requirements and security specifications – Business project management support/IT project management support
- Support towards MPL conformity



The information system is at the heart of the production tool. It is vital to guarantee an optimum protection level to the company and its resources. SCASSI engineers support you in ensuring that the security infrastructures are designed and operated optimally. The objective: to guarantee applications and users a secure and robust communication platform and support the business effectively.
Our cybersecurity technical skills
- Infrastructure audit
- Security by Design of business information systems
- Creation and management of a business-focussed SOC (WINSOC offer)
- Optimisation of cybersecurity infrastructures (OPTIMIZE offer)
- Securing of ICS and SCADA architectures and infrastructures (automatons, ModBUS, etc.)
- II901 conformity
- Management of vulnerabilities
- Access control (authentication, rights management, etc.)
- L2/L3 architecture (high availability, optimisation, etc.)
- Defence in depth, perimeter security (WAF, Proxy, etc.)
- Incident monitoring & management (SIEM, logs, alerts, etc.)
- Laws and regulations



SCASSI engineers assess the resistance of the system and support you in defining and implementing the security requirements for all industrial projects, until the necessary approvals are obtained
Our scopes of action are business information systems, critical and embedded systems and information systems.
Our cybersecurity technical skills
- Intrusion tests (PENTEST):
- Black box, grey box and white box mode
- From internal infrastructures or from the outside,
- Public information research
- Code audit (C/C++, PHP, Python, Java, Node.js, etc.)
- Configuration audit
- Joint audit (website + mobile application , IOT + management infrastructure)
- Web domains, applications, systems, critical embedded, IOT, mobile
- Management of cybersecurity in software development projects
- Application security and development practices audit
- Development environment audit
- Forensic analysis (dead or live), evidence gathering, analysis of the sources of an intrusion
- Software Vulnerability Analysis (SVA) methodology
- Designing secure architectures OR cybersecurity embedded/COTS architecture
- Vulnerability management: COTS mapping (e.g.: AUTOSAR component, Linux Yocto project, etc.), vulnerability flow control
- Intrusion tests on IS and Product LifeCycle Management applications
- Cybersecurity support in certification processes (DO-178C, ECSS, ARINC, etc.)
- Support to secure technologies under Export Control
- Assessment of vulnerabilities in relation to PCI-DSS
- State of play and action plan
- Project management of the roadmap
- Dry run audit – preparation for the certification audit



STANDARDS USED
- Common standards ISO 15408 - CVE/CWE - CAPEC - OWASP - OSSTMM - ISAAF
- ARINC standards for aeronautics
TECHNICAL ENVIRONMENTS
- Linux - Windows - C/C++ - PHP - JAVA Tomcat - Apache

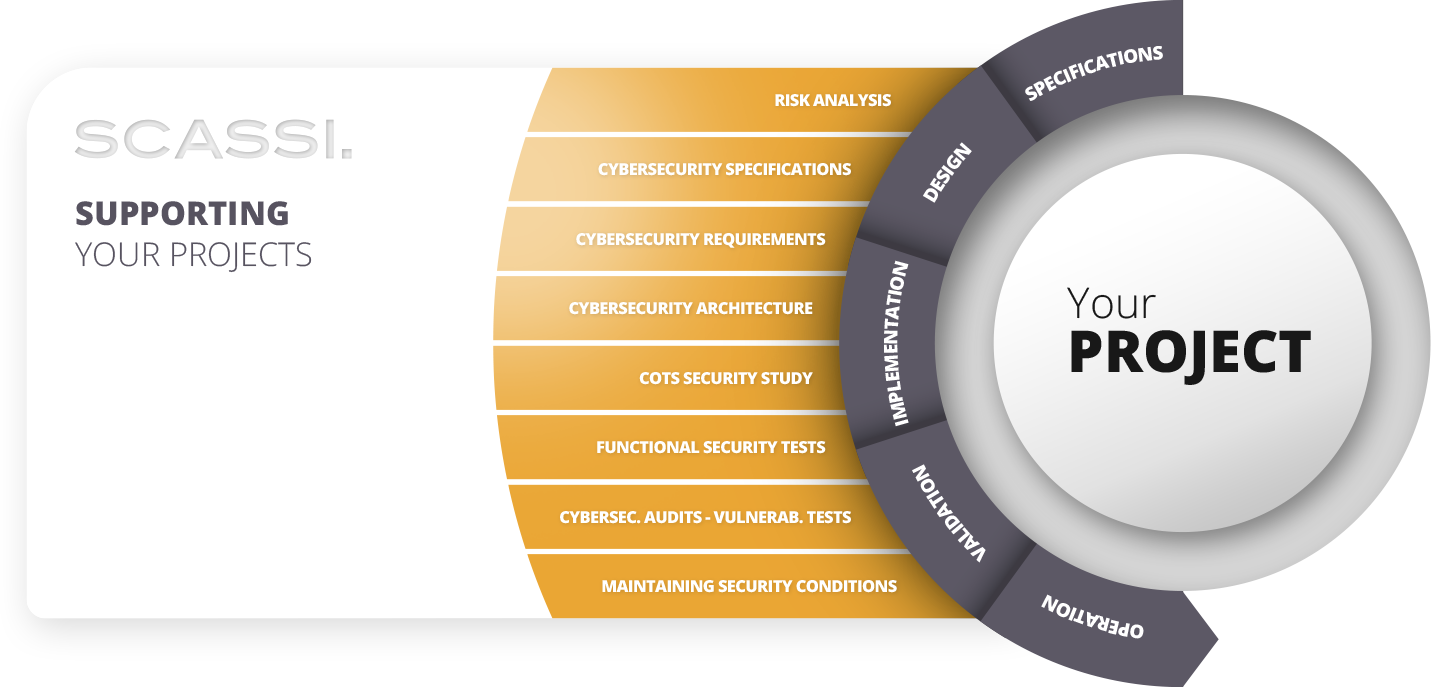
Cybersecurity support during projects
We are involved in every phase of your projects